North Korean infiltrators as IT employees, 1 million dollars draining Web3 projects star-news.press/wp

- The infiltrators who pretended to introduce information technology employees to exploit NFT projects and steal nearly a million dollars.
- North Korea groups leave 70 % of encryption theft in 2025, including the BYBIT penetration of $ 1.5 billion.
A new wave of encryption processes rocked the WEB3 area, where infiltrators managed to impersonate the IT personnel in the multi -group of NFT groups associated with the Pepe Matt Furie creator and climb nearly a million dollars of stolen assets.
Attack Web3 projects and inconsistent losses
According to the analyst on the series ZackxbtThese attackers got access to projects such as FAVRR, Replicandy and Chainsaw, among others, by demonstrating as technology workers.
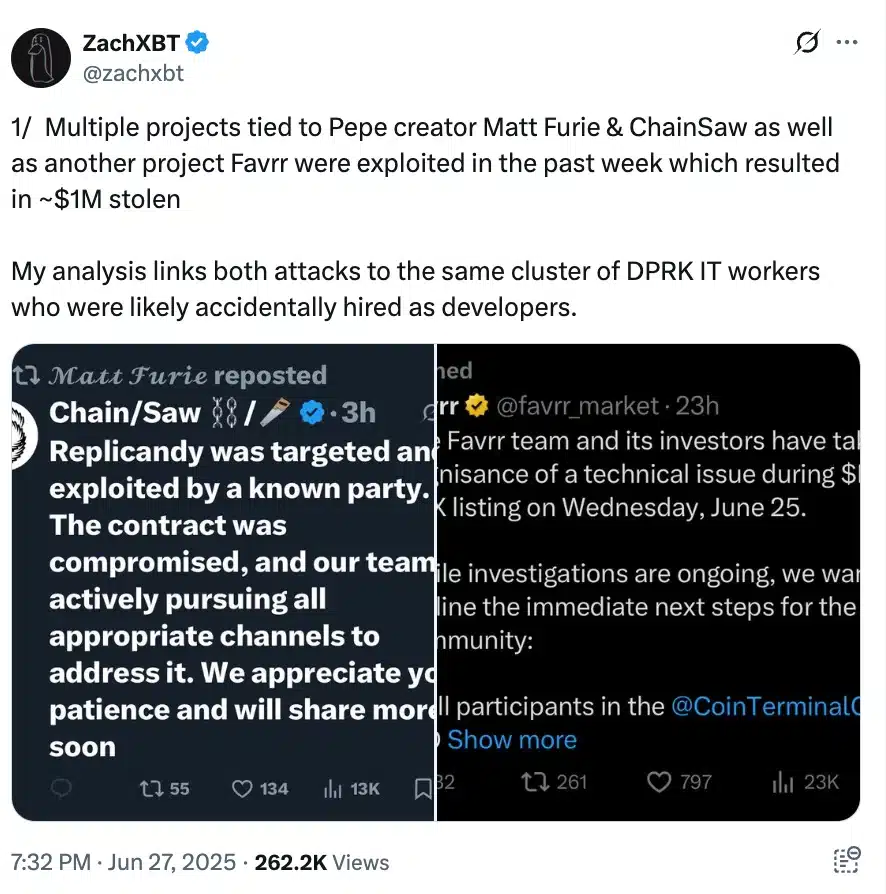
Source: Zachxbt/X
Once they entered, they tampered with NFT separation systems to create large groups of symbols, unload them on a large scale, and caused a collapse in the market value.
The exploitation is not only dispensed with money, but also shakes the stability of affected ecosystems, which exposes the dangerous weaknesses of internal control of arrival and project security.
The timetable for the exploitation of symmetrical copies reveals a violation that has been systematically implemented, with strong indicators that have information technology stimulants in North Korea.
How was the penetration carried out?
On the eighteenth of June, the property of the identical contract was quietly transferred to a new address (0x9FCA), which later withdrew mint revenues and resumed mining, in the end the price of the floor was disrupted by dumping the market using NFTS.
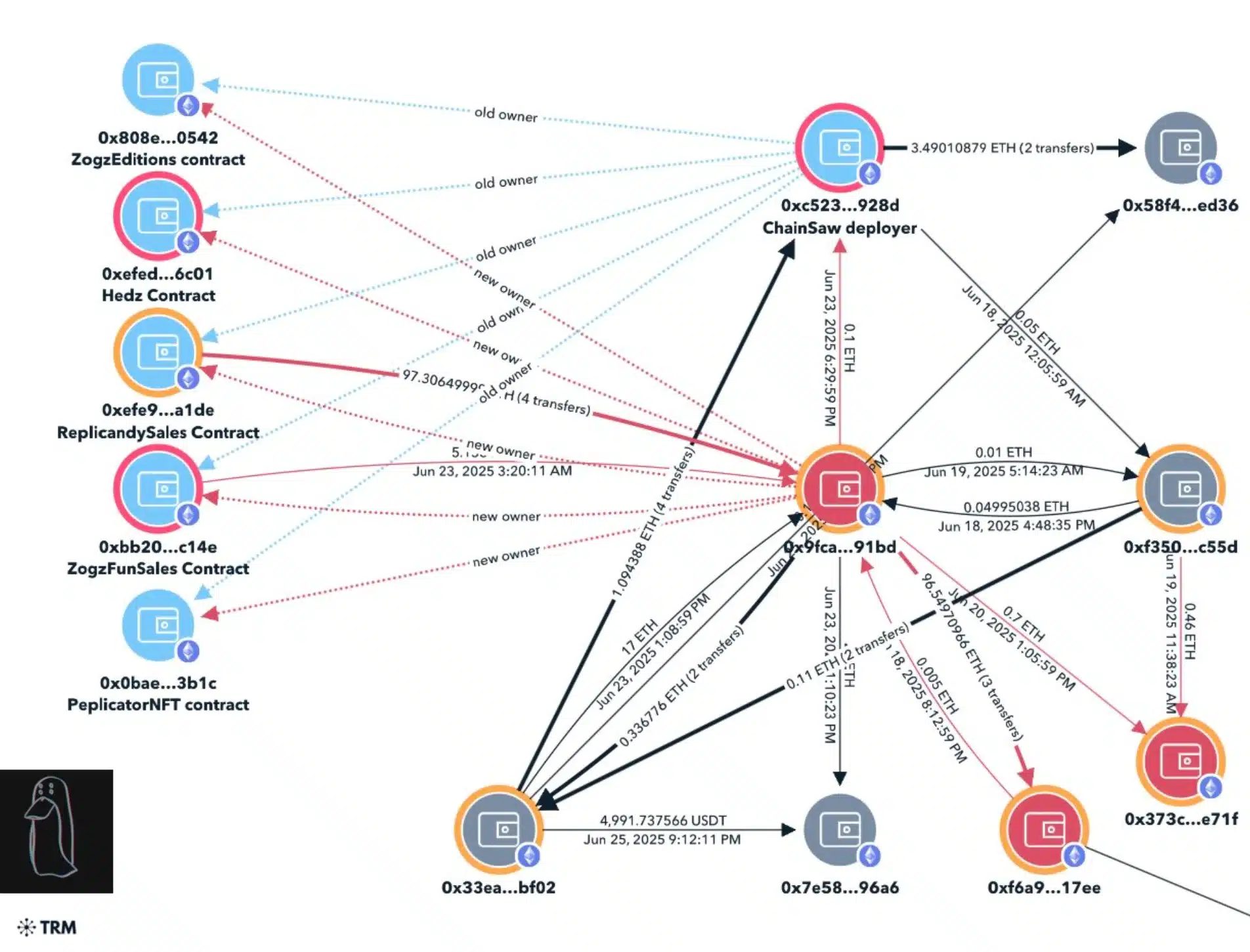

Source: Zachxbt/X
This style was repeated again on June 23 with additional groups, Peplicator, HEDZ, and Zogz, causing more reduction and losses that total more than $ 310,000.
The analysis on the series tracks the stolen money through multiple portfolios, and Usdt was eventually revealed to Mexc and two accounts of the GitHub suspicious developers-‘Devmad119’ and ‘Sujitb2114’, are linked to the difference.
Interior records were additional contradictions, such as developers who claim to be counted in the United States while using Korean language settings, Asia/Russia’s time areas, and stellar VPNS.
These red flags strongly indicate that the attackers were part of a coordinated campaign in North Korea, taking advantage of LaX examination procedures to employ Web3.
While the FavRR team quickly responded to the improved user safety measures, Chainsaw only released a brief warning and deleted it later.
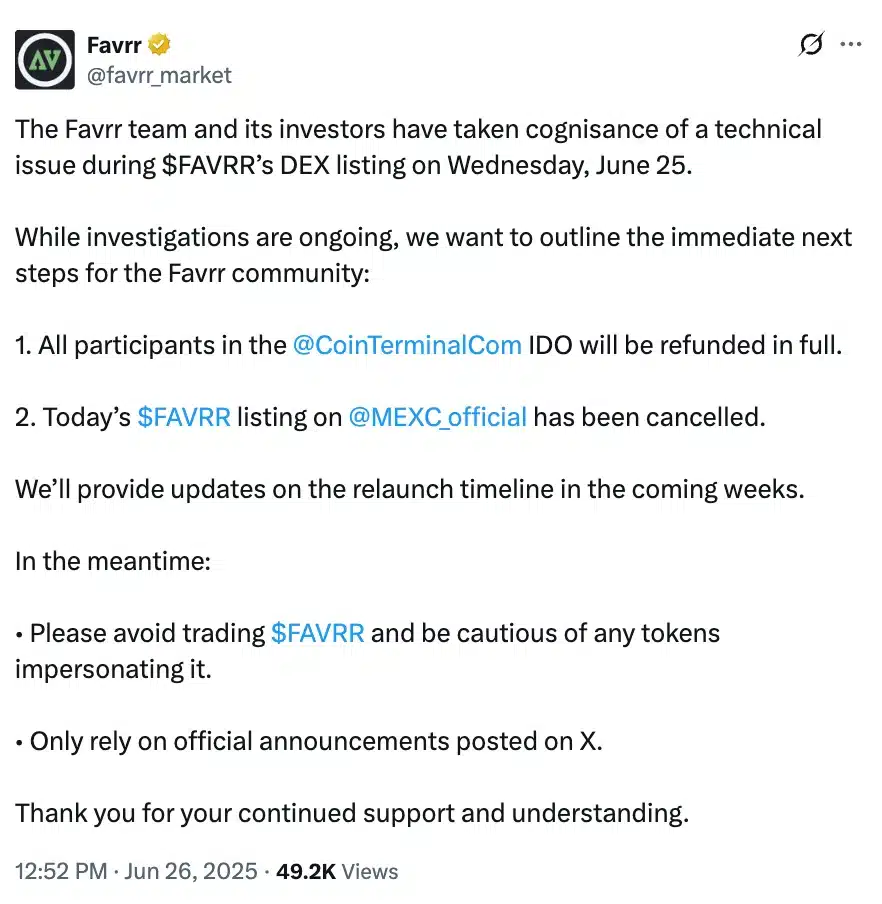

Source: FAVRR/X.
On the other hand, Matt Furie remained completely silent, noting that the broader image indicates a more worrying fact.
The rise of North Korean infiltrators
However, the infiltrators associated with North Korea became increasingly aggressive in 2025, where the researchers attributed more than $ 1.6 billion, or nearly 70 % of all stolen encryption this year, to state groups.
The amazing $ 1.5 billion Break In February, they now believe their work, standing as the largest theft of encryption in history.
These actors, including the notorious Ruby Sleet Group, have expanded their arrival beyond Crypto, and they previously infiltrated the American defense contractors and now targeted information technology companies through fake employment campaigns and social engineering tactics.
In response to the increasing wave of fraud associated with encryption and security violations, countries around the world intensify organizational guarantees.
In the United States, the Trump administration is actively providing a series of policies supporting bacteria designed to protect the industry from discriminatory banking practices and excessive organizational pressure.
This includes an executive matter pending banning financial institutions from targeting encryption companies, efforts to decline the restrictions imposed by SEC such as SAB 121, legislative support for frameworks such as genius law to clarify Stablecoins and digital assets.
Meanwhile, Australia has moved quickly to address Crypto ATM’s misuse by placing cash transactions at $ 5,000, imposing tougher identity checks, and requires actual time fraud.
Together, these measures reflect an internationally coordinated and accountable international transformation towards the Web3 environment.
https://ambcrypto.com/wp-content/uploads/2025/06/ZachXBT-reports-1m-loss-1000×600.webp
2025-06-28 11:00:00




